
Breached Passwords and Modern Authentication: How Clerk Protects Your App from Known Risks
TL;DR
Using passwords found in previous breaches is like leaving your door unlocked for attackers. Developers can stop this risk cold—tools like Clerk Authentication and its competitors (Auth0, Okta, Microsoft Entra ID, and others) automatically block known breached passwords during signup and reset. Let’s break down why this matters, what the latest password dumps look like, and how you can protect your users (and your reputation) in a few lines of code.
The Real-World Risk: “123456” Is Still Out There
Despite years of warnings, the same weak (and now breached) passwords top the charts every year. Billions of credentials—usernames and passwords—are exposed on the dark web from company breaches, phishing attacks, and database leaks. Attackers grab these lists and run credential stuffing attacks: they try stolen logins across other sites, hoping someone reused their password.
Just how bad is it?
Here are the current top 20 passwords from the latest breach dumps:
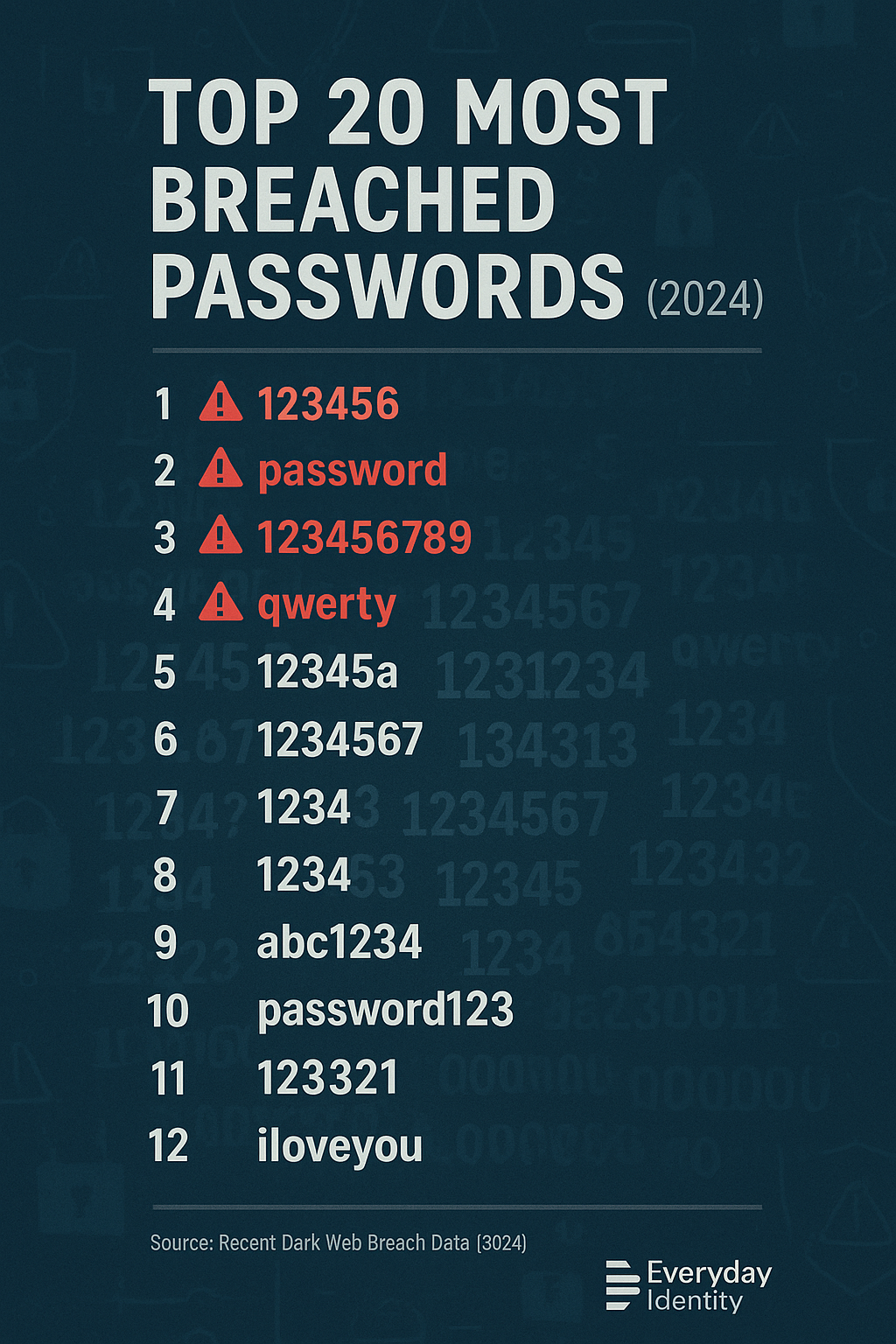
- 123456
- password
- 123456789
- 12345
- 12345678
- qwerty
- 1234567
- 111111
- 123123
- abc123
- 1234
- password1
- 12345a
- 654321
- qwerty123
- 1q2w3e4r
- 123321
- password123
- 000000
- iloveyou
It’s not just lazy users—attackers know people keep choosing these, and automation makes testing them trivial.
Why Breached Password Blocking Matters
Many people don’t realize:
- If you pick a password that’s been leaked, it doesn’t matter how long or complex it looks—if it’s in an attacker’s list, you’re vulnerable.
- Attackers use automated tools that can try millions of passwords in seconds, bypassing “guess limits” by spreading attempts over many accounts.
So what can you do as a developer or product owner?
Block the bad passwords before they’re even used.
Breached Password Detection Across the Industry: Who Does It and How
Clerk isn’t alone in fighting the scourge of reused and breached passwords. Let’s look at other major authentication and password management providers—and how their breached password detection features compare.
1. Auth0
- How it works:
Auth0 integrates directly with the Have I Been Pwned (HIBP) API to check user-chosen passwords against a constantly updated breach database. - Features:
- Automatic check at sign-up and password reset.
- Optionally block or warn users when a password appears in breaches.
- Custom actions allow developers to fine-tune the workflow.
- Developer impact:
Simple toggle in dashboard or via rule; robust API for customization.
2. Okta
- How it works:
Okta’s Password Policy can be configured to disallow passwords from known breached lists, leveraging proprietary and third-party data. - Features:
- Built-in breached password protection for Okta-hosted and custom login pages.
- Enforcement via policy configuration—no code required.
- Monitors password changes and self-service resets.
- Developer impact:
Enterprise-grade; scalable for large user bases.
3. Microsoft Entra ID (Azure AD)
- How it works:
Microsoft Entra ID includes Smart Password Protection with a global banned password list (containing breached and weak passwords) and organization-specific custom banned lists. - Features:
- Enforced at cloud and hybrid (on-prem + cloud) scale.
- Blocks passwords found in global breach datasets and those similar to them.
- Syncs with on-prem AD.
- Developer impact:
Policy-driven; applies across M365, Azure, and federated apps.
4. AWS Cognito
- How it works:
AWS Cognito allows custom password policies and recently added password breach detection (March 2023). - Features:
- Blocks or warns when a user selects a breached password.
- Leverages AWS-managed breach datasets.
- Can integrate with Lambda for more custom flows.
- Developer impact:
Ideal for serverless stacks; managed at the user pool level.
5. 1Password (Consumer & Business)
- How it works:
1Password checks saved and suggested passwords against HIBP’s “Pwned Passwords” API and issues warnings directly in the app or browser extension. - Features:
- Notifies users when any of their stored passwords appear in a breach.
- Recommends immediate password change.
- “Watchtower” dashboard gives risk overview.
- User impact:
Empowers end-users, not just app developers.
6. Other Notable Mentions
- Google Account Security: Google warns users if their password is found in a data breach, integrating with Chrome’s Password Checkup.
- Bitwarden, Dashlane: Similar breach detection with user and business reporting.
How Do These Services Differ?
- Integration depth: Some are backend-only (Clerk, Auth0, Okta), while others (1Password, Chrome, Bitwarden) alert end-users across all logins.
- Customizability: Most developer-focused platforms let you decide whether to block or only warn users; consumer tools often just report.
- Data source freshness: Leaders like Auth0, Clerk, and Microsoft update breach datasets regularly (often daily) via APIs from trusted sources.
Clerk and Breach Detection: Instant Security for Developers
While many platforms offer breached password detection, Clerk Authentication makes it especially easy for modern web and mobile app developers to plug in protection with minimal code or config. Here’s what sets Clerk apart:
- Fast integration: Get breach checks running in minutes—no API key for HIBP or custom workflows needed.
- Real-time: Checks happen instantly during signup, login, or password reset.
- User experience: Users are given a clear message and guided to pick a safer password.
// Example Clerk config (pseudo-code)
clerk.auth({
password: {
checkBreached: true, // Enforce breach checks!
minLength: 12,
requireNumbers: true,
requireSymbols: true
}
});
Check the Clerk docs for exact implementation steps.
Human Nature, Security Reality
We all want frictionless logins, but protecting users from themselves is part of your job. Even tech-savvy users fall into password reuse habits—especially when forced to change passwords often. Breach-blocking isn’t about blaming users; it’s about building resilient systems.
Takeaways
- Breached passwords are everywhere. Don’t let your app be the next easy target.
- Whether you use Clerk, Auth0, Okta, AWS Cognito, or Microsoft Entra ID, breached password detection is now a best practice—and expected for any serious app or platform.
- Tools like these make it simple for developers to enforce “never before seen” passwords—no homegrown breach lists or manual checks.
- If you’re building or running any app that stores user credentials, enabling breached password checks is the bare minimum for modern security.
🚦 Want to level up your password hygiene?
- Use a password manager
- Enable 2FA/MFA everywhere
- Educate your users
Stay safe—one login at a time.