Series format: Three levels × two posts each.
Post 1 (per level) = IAM — access, SSO, MFA/passkeys, device/risk checks, lifecycle (JML), SCIM, and PIM/JIT.
Post 2 (per level) = IGA — access reviews/certifications, SoD, policy, audit evidence, and continuous assurance.
Why this series—and why now
Identity work breaks when teams buy governance before they stabilize access, or when they over-index on a single vendor instead of designing for outcomes and clean handoffs. This series gives you a right-sized path for Startups/Small, Mid-Market, and Enterprise/Large organizations—so you can move fast without painting yourself into a corner.
We’ll keep it vendor-agnostic in principle, opinionated where it helps, and compliance-aware throughout (mapping choices to NIST CSF 2.0, SP 800-53, SOC 2, and ISO 27001 at a control-objective level). HR is treated as API-first and interchangeable: whether you run Workday, BambooHR, UKG, Gusto, or something custom, the patterns hold.
IAM vs. IGA (and why we separate them)
- IAM is how you run access. Think SSO, phishing-resistant MFA, passkeys, device compliance feeding policy, JML automation, SCIM, and PIM/JIT to eliminate standing admin.
- IGA is how you prove and govern access. Think periodic certifications, SoD guardrails, policy attestation, evidence pipelines, and continuous audit readiness.
Trying to govern chaotic access is like auditing a moving train. So we implement IAM first (stability, speed, safety), then layer IGA (proof, policy, assurance) with minimal rework.
Tracks you can follow (choose one—or mix)
Track A — Microsoft-first
Built on Entra ID/M365/Azure/Intune (with or without on-prem AD). Strengths: device posture → Conditional Access, rich admin controls with PIM/JIT, and broad enterprise integrations.
Track B — Google-first
Centered on Google Workspace/Cloud Identity and Context-Aware Access. Strengths: web-first productivity, simple passkey flows, and clean admin UX. Add an adjunct IdP or directory if you need broader SSO/LDAP/MDM.
Hybrid (the majority pattern)
Use the best of both: e.g., Okta for SSO/SCIM breadth with Entra as the “trust gate” (device, CA, PIM), or Workspace for productivity with Okta/JumpCloud to widen SSO and directory reach. Hybrid isn’t messy if you define who does what.
Outcomes ladder (applies to every level)
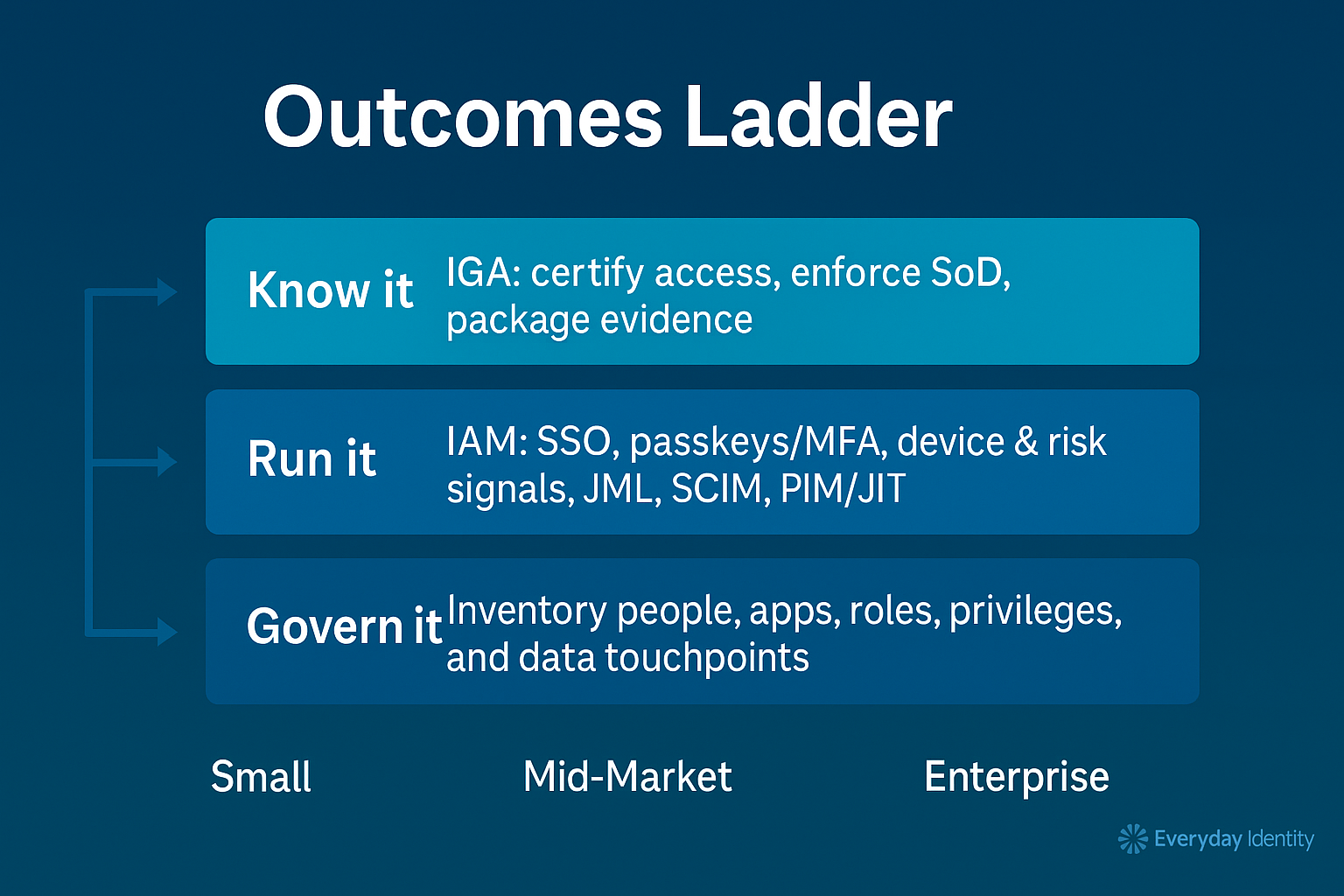
Every decision in the series rolls back to these three layers: know, run, govern.
What “good” looks like (KPIs that don’t care which tool you use)
- Phishing-resistant auth coverage ≥ 98% (passkeys/FIDO2 or equivalent signals).
- SSO coverage of your top apps: ≥ 80% (Small), ≥ 90% (Mid), ≥ 95% (Enterprise).
- Deprovision SLA from HR term: ≤ 15 minutes (Small); ≤ 5 minutes (Mid/Ent).
- Standing privileged access ≈ zero; PIM/JIT on ≥ 95% of admin roles.
- Certification completion ≥ 95% in 10 business days once IGA is live.
- Evidence pull time: ≤ 1 day (Mid), ≤ hours (Enterprise).
These aren’t vendor features—they’re operational habits. We’ll show multiple ways to hit them.
The three levels we’ll cover
1) Startup / Small (≈ 1–150 people)
- Post Small 1 — IAM: A no-regret starter: centralized sign-on for the top apps, passkeys or strong MFA, a password manager strategy (no shared accounts), and API-driven offboarding you can run in minutes.
- Post Small 2 — IGA: Lightweight governance: quarterly attestations, simple SoD for finance/dev separations, and an evidence log you can export without buying a platform on day one.
Why this order: You need speed, clarity, and safe offboarding more than you need dashboards. We’ll keep the governance habit small but real.
2) Mid-Market (≈ 150–2,000 people)
- Post Medium 1 — IAM: HR-driven lifecycle (API/webhooks from HR to IdP), group-based access with SCIM to your top 20 apps, device compliance gated for admin roles, and PIM/JIT to crush standing privilege.
- Post Medium 2 — IGA: Operational governance: risk-tiered certifications, pragmatic SoD (finance/dev/cloud), and automated evidence to your SIEM/GRC.
Why this order: Kill the ticket treadmill, then make reviews boring and predictable.
3) Enterprise / Large (2,000+ & regulated)
- Post Enterprise 1 — IAM: Platform-first identity: IdP + IGA + PAM + CIEM, multi-cloud privilege right-sizing, and a reference architecture that survives M&A.
- Post Enterprise 2 — IGA: Continuous compliance & resilience: live control mapping (NIST/ISO/SOC), purple-team exercises for identity attacks (MFA fatigue, token theft), and clean evidence in hours.
Why this order: Align platform choices to risk and regulation, then industrialize proof.
The Hybrid “handshake” (done right)
- IdP: People, groups, app federation, SCIM to SaaS.
- Trust gate: Conditional/Context-Aware Access that consumes device posture and risk to make decisions.
- Lifecycle: API-connected HR triggers joiner/mover/leaver events that flow to IdP → groups → SCIM → apps.
- Governance: Certifications & SoD feed decisions back to the systems that enforce access (remove group, revoke role, expire elevation).
- Evidence: Logs and approvals flow to SIEM/GRC for continuous assurance.
When responsibilities are explicit, hybrid becomes an architecture, not an accident.
Common traps this series will help you avoid
- Buying IGA before you stabilize IAM. Certifying chaos is still chaos.
- Hard-wiring entitlements to people, not groups. That’s future technical debt.
- Skipping device posture for admins. No compliant device → no elevation.
- Endless pilots. We’ll time-box to 6–8 weeks, lock patterns, and scale.
- Treating evidence as an afterthought. Start a minimal approval + change log on day one.
What you’ll get in each post
- A 90-day plan with week-by-week milestones.
- Microsoft-first, Google-first, and Hybrid callouts—balanced, not biased.
- 3–5 product comparisons per level (what they’re best at, tradeoffs, and when we’d choose them).
- Visuals you can paste into runbooks: small diagrams, quick checklists, and a KPI mini-dashboard.
- Clickable links to official product pages (collected at the end).
How to use this series
Pick your level and track, then copy the IAM Post 1 plan into your backlog. Once IAM is stable and you’re hitting SLAs, move to IGA Post 2. If you’re hybrid or mid-migration, use our “exit ramps” to adopt the next piece without re-platforming.
If you lead security or IT, share the KPI list with execs. If you’re hands-on, start with the SCIM and group patterns—they unlock almost everything else.
What’s next
We’re kicking off with Startup/Small — Post S1 (IAM): a practical starter that centralizes sign-on, deploys passkeys/strong MFA, codifies JML with your API-connected HR, and makes offboarding a five-minute, no-drama task. Then we’ll move to Post S2 (IGA) to stand up lightweight certifications and evidence without bloat.
Subscribe and follow along—every post will be implementation-ready.
Software mentioned (official links)
- Microsoft Entra ID — https://www.microsoft.com/en-us/security/business/identity-access/microsoft-entra-id
- Google Cloud Identity / Workspace — https://cloud.google.com/identity • https://workspace.google.com/
- Okta Workforce Identity — https://www.okta.com/products/workforce-identity/
- JumpCloud — https://jumpcloud.com/
- Softerra Adaxes — https://www.adaxes.com/
- Linx Identity Security Platform — https://www.linx.security/
- SailPoint (IdentityNow / IIQ) — https://www.sailpoint.com/
- Saviynt — https://saviynt.com/
- CyberArk — https://www.cyberark.com/
- Delinea — https://delinea.com/
- Veza — https://veza.com/
- Wiz — https://www.wiz.io/